Winter Viper APT Aiming to Exploit Zimbra Vulnerability in European Government Entities
On March 31, 2023, Ravie Lakshmanan wrote about Cyber Espionage and APT.
Winter Vivern, a notorious cyber attacker, has recently shifted its focus to target government officials in both Europe and the United States. This is part of a continuous operation to gather intelligence through illicit means.
According to a recent report from Proofpoint, TA473 has been exploiting an unpatched Zimbra vulnerability in webmail portals that are visible to the public since at least February 2023. As a result of this, the group has been able to access the email mailboxes of various government entities in Europe constantly.
The security company is keeping an eye on the actions of a group named TA473 (also known as UAC-0114). They are labeled as a hostile team whose goals seem to be in line with the political aims of both Russia and Belarus.
Despite its lack of complexity, the group's persistence has been evident in its recent attacks on state authorities in Ukraine and Poland, as well as government officials in India, Lithuania, Slovakia, and the Vatican.
The recent surge of hacking attempts linked to NATO involves taking advantage of CVE-2022-27926 (which has a CVSS score of 6.1). This vulnerability has been fixed, but it was initially a moderate-risk flaw in Zimbra Collaboration that could have given hackers without authentication the ability to run any HTML or JavaScript code they wanted.
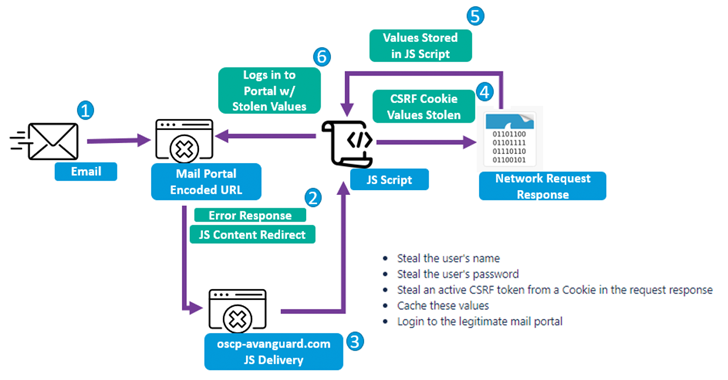
Another aspect of this process is the utilization of scanning software, such as Acunetix, in order to detect webmail portals of specific organizations that have not been updated. The purpose of this is to be able to send phishing emails disguised as trustworthy government agencies.
The notices contain deceitful web links that take advantage of a flaw in Zimbra called cross-site scripting. This flaw allows for custom JavaScript commands to be executed in the targeted email portals through Base64 encoding. This can expose sensitive information, such as usernames, passwords, and access tokens.
It is important to mention that every JavaScript bundle is specifically made for the internet messaging platform that is being targeted. This shows that the person responsible for the threat is willing to dedicate their time and money to ensure that they are not caught.
Proofpoint stated that TA473's success is largely contributed to their continuous efforts to scan for weaknesses and exploit unaddressed vulnerabilities in webmail portals that are accessible to the public.
The team puts all their efforts into thorough investigation and examination of public webmail portals to decipher the code of JavaScript. This code can steal confidential data such as usernames, passwords, and CSRF tokens which reveals their strong interest in finding ways to attack particular targets.
The discoveries were made amidst the disclosure that a minimum of three Russian intelligence organizations, which comprise FSB, GRU (tied to Sandworm), and SVR (tied to APT29), are suspected of utilizing hacking tools and software created by an IT provider based in Moscow referred to as NTC Vulkan.
Transform into an expert in Incident Response!
Discover the keys to a foolproof incident response plan by mastering the six-phase process with Asaf Perlman, Cynet's expert in incident response!
Make sure you don't miss the chance to secure your spot. Grab your seat now!
Some of the frameworks that are used by hackers for cyber attacks include Scan, which maps out enemy networks and allows for the gathering of large amounts of data. Another framework called Amesit is used to perform information campaigns and influence public opinion. Additionally, there is Krystal-2B which is utilized to simulate coordinated cyber attacks on transportation systems such as rail and pipeline control systems.
According to cybersecurity firm Mandiant, Krystal-2B is a training tool that performs simulations of OT attacks on various types of OT systems. This tool works together with certain IO components, and utilizes a technology called Amesit to intentionally cause disruptions.
The threat intelligence company stated that the contracted plans obtained from NTC Vulkan provide an understanding of how Russian intelligence services have invested in improving their abilities to carry out more efficient operations during the initial stages of an attack. This is a part of the operation that is often concealed from our sight.
SEKOIA.IO, a cybersecurity firm from France, conducted an evaluation of the cyber attack tools and named Amesit as an "information apparatus." This device was created to generate, spread, and enhance information across various platforms like SMS, social media, blogs, and forums.
This feature set comprises functions for catching, hindering, or modifying transmitted messages that go through communication devices, like routers or switches, and even sending internet service provider users to certain web pages.
According to SEKOIA.IO, Amesit is an example of how the Russian military employs a method known as the information warfare doctrine. This approach involves utilizing cyber attacks, electronic warfare, psychological tactics, and information manipulation in order to achieve strategic objectives.
Enjoyed reading this article? Stay updated with our latest exclusive posts by following us on Twitter and LinkedIn.





























































